Accelerate Productivity in 2025
Reignite Growth Despite the Global Slowdown
With the increase in the number of connected devices, especially the Internet of Things (IoT) devices, the risks of cyber attacks are also growing. Security teams are tackling software and network vulnerabilities and hardware-level bugs with technological advances. We give you a comprehensive view of global cybersecurity trends so that you can follow the latest developments in the industry. For example, IT teams are transitioning to automated threat detection and response workflows to mitigate malicious attacks. Read more to explore the top trends impacting the cybersecurity sector.
Innovation Map outlines the Top 10 Cybersecurity Trends & 20 Promising Startups
For this in-depth research on the Top Cybersecurity Trends & Startups, we analyzed a sample of 3 395 global startups and scaleups. The result of this research is data-driven innovation intelligence that improves strategic decision-making by giving you an overview of emerging technologies & startups in the cybersecurity industry. These insights are derived by working with our Big Data & Artificial Intelligence-powered StartUs Insights Discovery Platform, covering 2 500 000+ startups & scaleups globally. As the world’s largest resource for data on emerging companies, the SaaS platform enables you to identify relevant startups, emerging technologies & future industry trends quickly & exhaustively.
In the Innovation Map below, you get an overview of the Top 10 Cybersecurity Trends & Innovations that impact 3 395 companies worldwide. Moreover, the Cybersecurity Innovation Map reveals 20 hand-picked startups, all working on emerging technologies that advance their field.
Top 10 Cybersecurity Trends in 2023
- Automated Threat Management
- Cloud Security
- Zero-Trust Architecture
- Identity Management
- Behavioral Analytics
- Cyber Governance
- Endpoint Protection
- Cybersecurity as a Service
- Blockchain Security
- Cybersecurity Mesh
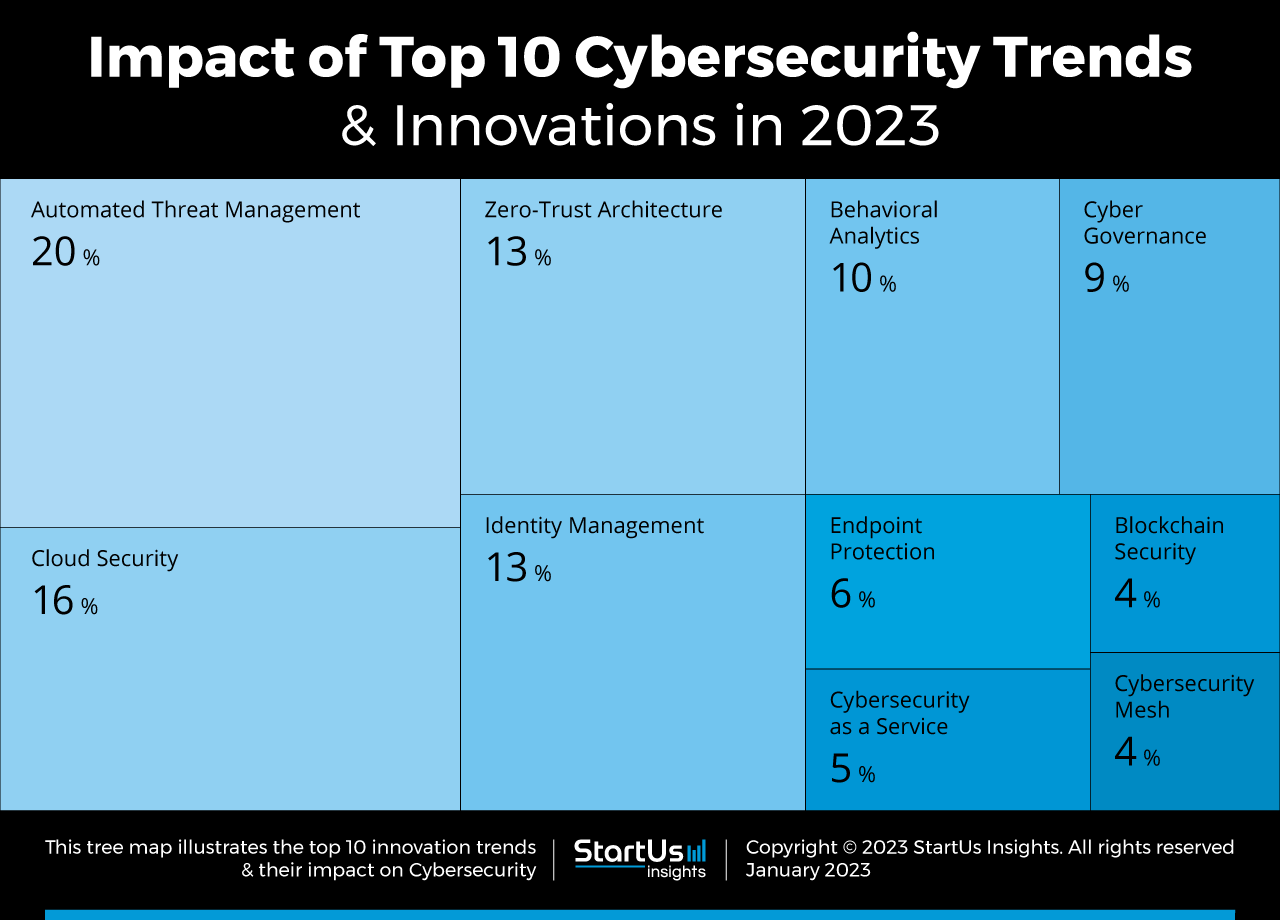
Tree Map reveals the Impact of the Top 10 Cybersecurity Trends
Based on the Cybersecurity Innovation Map, the Tree Map below illustrates the impact of the Top 10 Cybersecurity Trends in 2023. Artificial intelligence (AI), machine learning, and deep learning is powering automated threat management. The industry is also focusing on identity management, cyber governance, and endpoint protection. As businesses move to the cloud, there is a rise in cloud security solutions impacting cyberspace. Zero-trust architecture (ZTA) augments identity management to reduce cyber risks due to unauthorized devices. Additionally, cybersecurity firms are transitioning from managed services to cybersecurity as a service (CSaaS) models. Such solutions allow companies to mitigate infrastructure costs and improve scalability while implementing cybersecurity measures. Lastly, blockchain security improves data security and cybersecurity mesh aids the scaling and management of cross-platform cyber risk management.
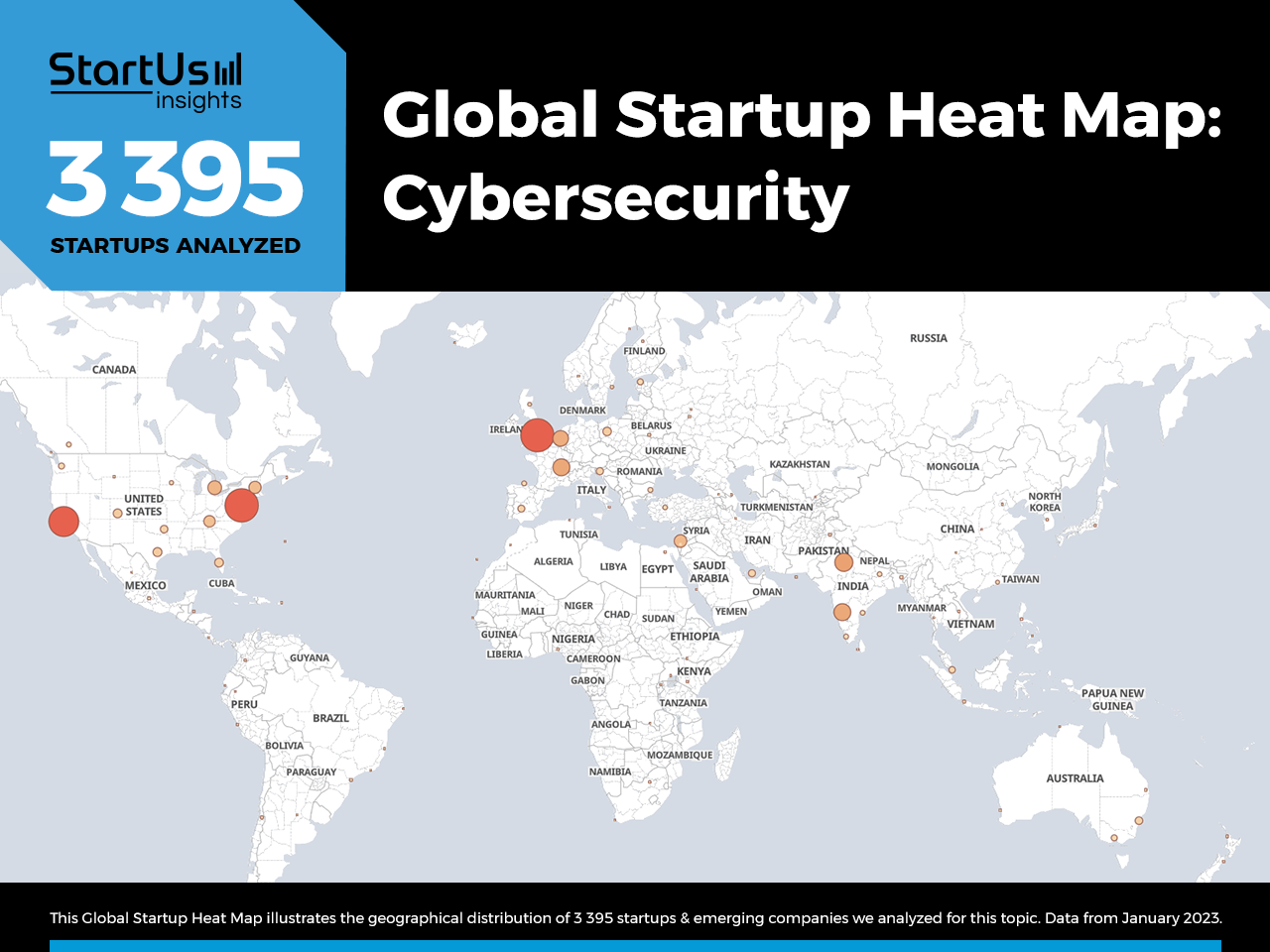
Global Startup Heat Map covers 3 395 Cybersecurity Startups & Scaleups
The Global Startup Heat Map below highlights the global distribution of the 3 395 exemplary startups & scaleups that we analyzed for this research. Created through the StartUs Insights Discovery Platform, the Heat Map reveals that the US and UK see the most cybersecurity startup activities, followed by India and other Western European countries.
Below, you get to meet 20 out of these 3 395 promising startups & scaleups as well as the solutions they develop. These cybersecurity startups are hand-picked based on criteria such as founding year, location, funding raised, and more. Depending on your specific needs, your top picks might look entirely different.
Top 10 Cybersecurity Trends for 2023
1. Automated Threat Management
Manual verification of users and devices is a time- and resource-intensive task due to the large number of devices connected to private and public networks. Besides, this approach is prone to manual errors and causes false positives. To tackle this, startups offer AI-based automated threat management solutions. They integrate into existing IT infrastructure to monitor data flows as well as device and user access. This enables admins to analyze massive amounts of data in real-time and leverage historic device or network data to stop suspicious activities. Consequently, such solutions reduce cyber risks and enable automated threat detection and response. Moreover, automated threat management shifts cybersecurity from passive workflows to predictive measures.
hyprfire aids Cyber Threat Hunting
Australian startup hyprfire develops Firebug, a threat hunting and network monitoring tool. It combines statistics and explainable AI to detect lateral movement, unauthorized computers, and baseline anomalies. This provides visibility into all connected devices in the network and identifies suspicious activities, allowing network security teams to prevent cyber risks.
CloudGuard provides Continuous Network Monitoring
CloudGuard is a UK-based startup that offers СloudGuard Security Lifecycle Platform, a continuous network monitoring solution. It uses AI to monitor, identify, and hunt threats as well as scan and test on-premise and cloud environments for security weaknesses. The platform alerts IT departments upon detecting anomalies. Consequently, this enables businesses to improve vulnerability and risk management, ensuring data integrity in multi-platform configurations.
2. Cloud Security
As more companies adopt a work-from-home (WFH) culture, there is an increase in the associated cyber risks it brings to businesses. That is why recent years see large startup activity in cloud security solutions. As organizations transition to multi-cloud configurations, individually managing their security is tedious. Startups develop cloud-native cybersecurity platforms that allow IT teams to manage security across cloud platforms. Besides, cloud security solutions enable administrators to apply bug fixes without depending on end users or third parties. Startups further develop encryption technologies, like homomorphic encryption, that mitigate the need for decryption to process data. These solutions significantly improve the cybersecurity of cloud-based services.
Lightspin offers Graph-based Cloud Security
Lightspin is an Israeli startup that provides graph-based cloud security. The startup’s multi-layer contextual security platform leverages attack-path analysis and graph theory algorithms. It aids visualization, prioritization, and remediation of potential attack paths and security gaps while improving visibility into cloud stacks. This allows security teams to reveal exploitable risks and centralize security management.
Cado Security aids Cloud Investigation
Cado Security is a UK-based startup that makes Cado Response, a cloud investigation platform. It automates data capture and processing to efficiently investigate and respond to cyber incidents. Moreover, it enables IT teams to improve cyber risk response across cloud, container, and serverless environments.
3. Zero-Trust Architecture
The number of connected devices is predicted to reach 14 billion by 2022. This takes the complexity of authenticating connection requests coming to networks to a staggering level. Therefore, the cybersecurity industry is emphasizing ZTA to eliminate the authorization of suspicious devices. As ZTA denies access to all devices by default, unless approved by the admin, it greatly reduces the risk of malicious hackers accessing critical data. Since this is a software-level implementation, zero-trust architecture does not require high capital expenses. Further, startups combine AI and ZTA to automate request processing to identify the authenticity and relevance of the request.
BastionZero offers Secure Cloud Access
BastionZero is a US-based startup that uses ZTA to ensure secure cloud access. The startup’s cryptographic, multi-root, zero-trust access protocol allows IT teams to offer remote cloud access without virtual private networks (VPNs). It integrates into existing single sign-on systems (SSO) to centralize policy management and logging. This enables system admins to mitigate overprivileged certificate authorities and long-lived credentials, improving access control.
Aerobyte Cyber makes a Cyber Defense Framework
Aerobyte Cyber is a US-based startup that creates a zero-trust software-defined perimeter (SDP). It leverages end-to-end dynamic tunnel encryption and zero-trust architecture to remove visibility into the internal network. Moreover, the SDP routes users through authorized resources to protect internal traffic. This, in turn, allow companies to reduce cyber risks and centralize cyber risk management.
4. Identity Management
An efficient identity and access management (IAM) system is necessary for IT teams to reduce false positives and negatives. As companies shift to hybrid IT environments, data and resources are becoming distributed across edge servers, cloud services, and on-premise installations. Startups offer identity management systems tailored for hybrid environments. This is vital because of the change in work culture and the increased number of devices connected to the networks. Startups further leverage multi-factor authentication (MFA) that assesses more than one user parameter like hardware id, previous activities, and biometrics, among others, improving identity management accuracy.
SonicBee offers Identity and Access Management (IAM) as a Service (IAMaaS)
SonicBee is a Dutch startup that provides IAMaaS for businesses. The startup’s solution, Intelligence Access Platform, allows security teams to manage access to on-premise and cloud environments. It automates access provisioning and de-provisioning as well as enables centralized control management. Companies use SonicBee’s IAM platform to manage devices in heterogeneous networks.
Authenly provides Offline Two-Factor Authentication (2FA)
Authenly is a UK-based startup that provides offline 2FA. The startup’s platform uses a secret key that stays in the device and a timed one-time password (TOTP) to authenticate users. It also encrypts the data to prevent malicious attacks. Moreover, the platform works while offline and authenticates users without internet connectivity. This allows companies to avoid access denials due to network issues and improve security.
5. Behavioral Analytics
As man-in-the-middle and phishing attacks become more common, security teams cannot rely only on password authentication for identity verification. This is where behavior analytics comes in, along with MFA. It leverages historic and real-time data to examine trends, patterns, and habits in user workflows. So, whenever a user or user’s device deviates from the standard workflows, behavior analytics solutions flag the activity and take necessary measures to avoid cyber risks. This enables a context-aware workflow in cyber risk management. Startups develop such solutions using machine learning or advanced analytics that alert IT teams upon detecting suspicious activities in their networks. Since the control of insider threat management is minimal, this risk-based approach significantly reduces data leaks from people within organizations.
Neosec offers Application Security
Neosec is a US-based startup that builds an application security platform. It leverages AI to collect and analyze data from application programming interfaces (APIs) for investigations and threat hunting. The platform’s behavioral analytics interprets normal and abnormal usage to detect misconfigurations, misuse, and business logic abuse. This enables IT admins to collect context-specific information and quickly respond to threats.
Foresiet aids Cyber Investigation
Foresiet is an Indian startup that makes a cyber digital investigator platform. Its AI-based engine monitors networks and devices to identify malicious activities like targetted attacks, breach credentials, and ransomware. Moreover, the platform allows network admins to design systematic continuous improvement plans (CIPs). Lastly, it provides insights into attack surface visibility, threat actors, and advisories.
6. Cyber Governance
User concerns around privacy are driving rapid changes in regulations and policies. Therefore, companies constantly need to audit their IT systems to ensure compliance and avoid penalties. To avoid this, startups are developing plug-and-play solutions to automate cyber governance. Such platforms continuously monitor databases and network security to find deviations and alert IT admins. Further, some startups offer AI-powered cyber governance platforms that mitigate human intervention in enforcing data policies. This allows organizations to avoid third-party audits and expensive managed services.
Dasera enables Continuous Data Governance
Dasera is a US-based startup that provides continuous data governance. The startup’s data security platform automatically monitors infrastructure contexts such as cloud data, misconfigurations, and new data fields. It generates data context through data classification and tagging as well as automates employee directory integration and permission analysis. This way, Dasera continuously enforces data governance policies and reduces cyber risks.
ISMAC facilitates Compliance Management
ISMAC is a US-based startup that simplifies compliance management. The startup’s solution, ISMAC USM, monitors policies, compliance, and configurations to keep digital assets compliant with industry data standards and regulations like PCI DSS requirements. It also features case management for IT security teams to investigate and respond to security incidents. Additionally, ISMAC USM supports log management, risk detection, and security monitoring. It, in turn, allows security teams to centralize cyber risk management and ensure data compliance.
7. Endpoint Protection
Organizations kept digital assets in their secure private network before hybrid work became the new normal. This shift to remote and hybrid work environments, and consequently cloud networks, is increasing cyber risks for employees and organizations. The number of ransomware attacks is also rising every year, where home systems are easy targets. This is why startups make endpoint protection solutions. Such solutions for employees and home users monitor network activities to identify malicious websites and data. Companies also leverage endpoint protection through hardware solutions that greatly improve the firewall capabilities of their networks. This allows companies and users to mitigate data recovery and legal costs.
BYTESEQ provides Anti-Ransomware Protection
BYTESEQ is an Indian startup that creates an anti-ransomware endpoint protection suite. It generates decoy assets throughout the infrastructure to trick cybercriminals into discovering vulnerabilities. Upon detecting triggers, the suite sends notifications to a centralized deception server that attacks the vectors used by cybercriminals. It also monitors systems in real-time to identify suspicious behavior and mitigate internal cyber risks. As a result, businesses are able to promptly detect and avoid expensive ransomware attacks.
OTTOSEC develops Automotive Endpoint Protection
OTTOSEC is an Israeli startup that makes endpoint protection hardware for automobiles as after-market installations and original equipment manufacturer (OEM) integrations. The startup’s low-cost, standalone, and in-vehicle device offers a stateful CANBUS firewall that identifies and prevents damage from cyberattacks. Moreover, the solution is managed centrally using a network security center. This, in turn, allows manufacturers and vehicle owners to ensure the safety of their automotive electronic systems, especially in a connected ecosystem, and reduce car theft.
8. Cybersecurity as a Service
The flexibility and scalability of cloud architecture enable startups to provide cybersecurity as a service. In addition, they use subscription models to offer secure hardware for companies. This enables organizations to move from capital-intensive IT infrastructure without disrupting operations. Besides, leveraging services from multiple vendors increases network redundancy. However, this trend is visible among the attackers as well where they sell ransomware as a service (RaaS) on the dark web. Therefore, it is crucial for small and medium businesses (SMBs) to leverage CSaaS to protect their network and data from growing cyber risks.
GAT InfoSec provides Exposure Surface Analysis
GAT InfoSec is a Brazilian startup that offers exposure surface analysis as a service. The startup’s product, GAT Security Score, leverages machine learning to automate risk diagnosis, evaluate suppliers, monitor digital assets, and assess third-party risks. It then generates a security score that indicates the level of exposure to threats and provides information on the exposed inventory, identifies vulnerabilities, and leaked data. Security teams utilize this data to mitigate data leaks, credential hijacking, and ransomware attacks, among others.
SecOps Solution offers Agentless Cybersecurity
SecOps Solution is a US-based startup that provides agentless security for IT infrastructure and applications. The startup’s solution offers cloud, container, and mobile app security as well as features vulnerability management, security audits, and compliance assessments. It also integrates with other business tools like Slack and email apps to improve vulnerability scanning. Moreover, the solution provides IT admins with context-based security assessments to reduce cyber incidents and false positives.
9. Blockchain Security
The immutability, traceability, and distributed architecture of blockchain enable transparent transactions and data sharing. While FinTech is the major player in leveraging blockchain, organizations are integrating blockchain-powered communication and data transfer systems to boost their data management practices. This allows IT teams to ensure data integrity. Moreover, leveraging blockchain to store encryption keys and data fingerprints greatly enhances security due to its immutable storage. For instance, recipients are able to verify data fingerprints through the blockchain network and identify network breaches due to man-in-the-middle attacks.
Verifoxx provides Blockchain-based Identity Verification
Verifoxx is a UK-based startup that offers blockchain-based identity verification. The startup combines a blockchain network and zero-knowledge-proof architecture to provide identity as a service. It uses computer vision and deep learning to scan identities and documents, whereas smart contracts enable decentralized, anonymous, and secure verification processes. This allows finance, health, and educational organizations to streamline identity verification while protecting sensitive customer information and staying compliant.
EAS Project enables Blockchain-based Customs Data Management
EAS Project is a Finnish startup that provides blockchain-based customs data management. The startup’s end-to-end software-as-a-service (SaaS) data platform connects online retailers, logistics companies, postal operators, and customs authorities. It provides customs datasets through its blockchain network to mitigate data fraud and optimize customs handling. As a result, all stakeholders are able to ensure seamless product deliveries and GDPR compliance.
10. Cybersecurity Mesh
Companies are utilizing a combination of cloud and edge environments as well as on-premise installations to improve operational flexibility and efficiency. This is why the cybersecurity industry is moving to scalable and integrated risk management models. Cybersecurity mesh allows IT teams to integrate all devices, platforms, and networks in a single point. Consequently, it provides an overall view of organizations’ IT assets and improves cyber risk management. Startups are building cybersecurity mesh solutions that enable a standard security structure to protect assets across all environments.
Naoris Protocol enables Decentralized Cybersecurity Mesh
Naoris Protocol is a Portuguese startup that provides decentralized cybersecurity mesh. The startup leverages the Ethereum blockchain and a proprietary decentralized app (dApp) to convert centralized computer networks into cryptographic validator and threat hunter nodes. This enables the nodes to constantly report their status under consensual trust across the network. As a result, the startup’s mesh allows IT teams to quickly detect risks and governance lapses, making organizational networks Web3-ready.
Exium provides Zero-Trust Network Security
Exium is a US-based startup that develops 5G-powered zero-trust network security solutions. The startup’s device and gateway software solutions secure internet, private, and internet of things (IoT) devices as well as software-defined wide area networks (SD-WANs). This integrated cloud security approach enables IT teams to mitigate multi-vendor security appliances while ensuring secure web gateways and intrusion prevention.
Discover all Cybersecurity Trends, Technologies & Startups
AI and advanced analytics play a significant role in tackling upcoming cyber threats and ensuring a safe work environment. Additionally, cloud security and cloud-based cybersecurity services are integral in accelerating cyber risk management adoption across small and large companies. The cybersecurity industry is also advancing quantum-proof technologies, zero-day vulnerability management, defensive AI, and homomorphic encryption. These solutions will be necessary for organizations to resist the constant threat from malicious hackers to mitigate data leaks and disruptions.
The Cybersecurity Trends & Startups outlined in this report only scratch the surface of trends that we identified during our data-driven innovation and startup scouting process. Among others, automated threat response, quantum cryptography, and Web3 will transform the sector as we know it today. Identifying new opportunities and emerging technologies to implement into your business goes a long way in gaining a competitive advantage. Get in touch to easily and exhaustively scout startups, technologies & trends that matter to you!


![10 Top Digital Twin Startups and Companies for Industry 4.0 [2025]](https://www.startus-insights.com/wp-content/uploads/2025/06/Digital-Twin-Startups-for-Industry-4.0-SharedImg-StartUs-Insights-noresize-420x236.webp)